Table of Contents
- Fundamentals of Chip Technology
- Secure Element: The Vault
- Operating System: The Conductor
- Step‑by‑Step Transaction Flow
- 1. Card Detection and Application Selection
- 2. Initiate Application Processing
- 3. Data Retrieval
- 4. Cardholder Verification
- 5. Generate a Dynamic Cryptogram
- 6. Authorization Request
- 7. Response and Completion
- Why the Chip Is More Secure Than a Magnetic Stripe
- Contactless Payments and Tokenization
- Impact on Everyday Users
- Future Developments
The moment you slide your credit card through a payment terminal, a tiny microprocessor inside the plastic begins a complex dance of data exchange. This chip, often overlooked, is the cornerstone of modern card security, ensuring that each purchase is authenticated and encrypted in real time. Understanding how the chip on a credit card works reveals not only the engineering brilliance but also the layers of protection that keep your finances safe.
From its origins in the early 1990s to the ubiquitous EMV (Europay, Mastercard, Visa) standard that dominates today, the chip has evolved dramatically. Its ability to generate a unique transaction code for every swipe or tap distinguishes it from the magnetic stripe that preceded it. As merchants worldwide adopt chip-enabled terminals, the technology continues to adapt, supporting contactless payments, mobile wallets, and even tokenization for online shopping.
Fundamentals of Chip Technology
At the heart of a chip-enabled credit card lies a secure microcontroller, comparable to the processor in a smartphone but far more specialized. This microcontroller contains two essential components: a secure element and an operating system designed specifically for payment applications.
Secure Element: The Vault
- Encrypted Storage: Sensitive data such as the Primary Account Number (PAN) and cryptographic keys are stored in encrypted form, inaccessible to external software.
- Tamper Resistance: Physical and logical safeguards detect attempts to breach the chip, triggering self-destruct mechanisms that erase critical data.
- Key Management: Each card holds a unique set of cryptographic keys that are never shared, forming the basis for secure communication with the issuing bank.
Operating System: The Conductor
- Transaction Logic: Handles the sequence of commands from the terminal, including verification, authentication, and response generation.
- Application Selection: Supports multiple payment schemes (Visa, Mastercard, etc.) on a single card, allowing the terminal to choose the appropriate protocol.
- Compliance: Ensures each transaction adheres to EMV standards, which dictate how data is formatted, encrypted, and transmitted.
Step‑by‑Step Transaction Flow
When you present your card, the terminal initiates a series of messages that can be broken down into distinct phases. Below is a simplified, yet accurate, chronology of what happens behind the scenes.
1. Card Detection and Application Selection
The terminal reads the card’s contact interface (or contactless antenna) and requests a list of applications stored on the chip. The card responds with identifiers for each supported payment network. The terminal selects the appropriate application based on its configuration and the merchant’s processing preferences.
2. Initiate Application Processing
Once an application is chosen, the terminal sends a GET PROCESSING OPTIONS command. The chip replies with a set of data elements, including the Application Interchange Profile (AIP) and the Application File Locator (AFL). These elements tell the terminal what cryptographic capabilities the card possesses and where to find the necessary records.
3. Data Retrieval
Using the AFL, the terminal reads specific records from the chip that contain the cardholder’s PAN, expiration date, and other static data. This information is used to route the transaction to the correct issuer and to perform basic validation.
4. Cardholder Verification
Depending on the transaction amount and merchant settings, the terminal may request a PIN, signature, or rely on no verification for low‑value contactless payments. The chip processes the PIN locally, comparing it against the encrypted PIN stored in the secure element. A mismatch aborts the transaction before any network communication occurs.
5. Generate a Dynamic Cryptogram
The most critical security feature is the creation of a unique cryptogram—often called an Application Cryptogram (AC). Using the transaction data (amount, terminal capabilities, timestamp) and the card’s secret keys, the chip runs a cryptographic algorithm (typically Triple‑DES or AES) to produce a one‑time code. This code ensures that even if the transaction data were intercepted, it could not be reused.
6. Authorization Request
The terminal bundles the static data, the dynamic cryptogram, and other transaction details into an authorization request message. This message travels over the payment network to the issuing bank, which validates the cryptogram, checks the cardholder’s account status, and decides whether to approve or decline.
7. Response and Completion
The issuer sends back an approval or denial code, along with any additional instructions (e.g., online verification required). The terminal displays the result to the merchant and prints a receipt if needed. Throughout this process, the chip never reveals the secret keys, keeping the core of the security model intact.
Why the Chip Is More Secure Than a Magnetic Stripe
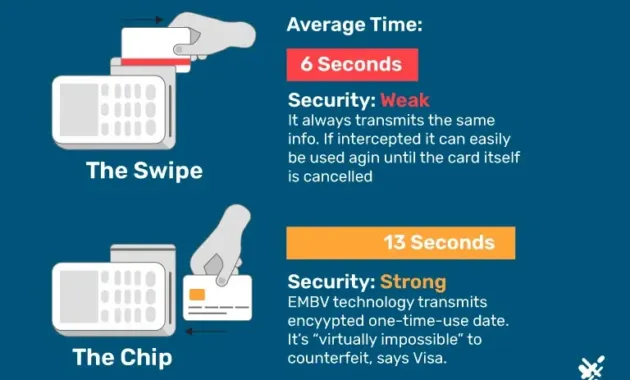
The magnetic stripe stores static data that can be copied with relatively simple equipment. Once duplicated, the counterfeit card can be used repeatedly until the issuer detects fraudulent activity. In contrast, the chip’s dynamic cryptogram changes with every transaction, rendering stolen data useless after a single use.
Furthermore, the chip’s secure element isolates cryptographic operations from the rest of the card, making it extremely difficult for attackers to extract or tamper with the keys. Even sophisticated skimming devices that read chip data cannot retrieve the underlying secrets, because the data transmitted during a transaction is encrypted and one‑time use only.
These security advantages have led to a rapid decline in card‑present fraud rates in regions that have fully adopted EMV. According to industry reports, countries like the United Kingdom and Canada have seen fraud losses drop by over 70% after widespread chip implementation.
Contactless Payments and Tokenization
Modern chip cards often support contactless functionality, allowing users to tap the card near a terminal without inserting it. The underlying process remains the same—dynamic cryptograms are generated—but the communication occurs over a short‑range radio frequency (NFC). This convenience does not compromise security because the same encryption and one‑time code principles apply.
When you add a chip card to a mobile wallet (such as Apple Pay or Google Pay), the wallet creates a token that replaces the actual PAN during transactions. The token, paired with a device‑specific cryptographic key, ensures that even if the token is intercepted, it cannot be used without the originating device. This additional layer of abstraction builds on the chip’s security model, extending protection to digital payments.
Impact on Everyday Users
For most cardholders, the chip operates invisibly. However, understanding its role can help users make informed decisions about security and convenience. For example, if a merchant offers a “swipe‑only” option, opting for the chip insertion can reduce the risk of fraud. Similarly, enabling contactless payments on your card can speed up checkout while preserving the same security guarantees.
When considering new credit cards, look for those that advertise EMV compliance, contactless capability, and additional security features such as purchase protection. Resources like Unlock Savings with Low Interest Rate Credit Card Options – Your Guide to Smarter Spending can help you compare cards that balance cost and security.
Future Developments

The evolution of chip technology continues as the payment ecosystem embraces biometric authentication, blockchain‑based settlement, and advanced tokenization. Emerging standards like EMV 3‑DS aim to provide richer data exchange for online transactions, bridging the gap between card‑present and card‑not‑present environments.
Additionally, research into quantum‑resistant cryptography may eventually replace the current algorithms used in chip cryptograms, ensuring that tomorrow’s threats cannot compromise today’s secure elements. While these advancements are still in development, the foundational principles—dynamic data, isolated secure elements, and strict adherence to standards—remain the bedrock of card security.
Understanding how the chip on a credit card works demystifies a technology that many of us use daily without a second thought. From the secure element’s vault‑like storage to the dynamic cryptogram that changes with every purchase, each component works in concert to protect both the consumer and the financial institutions behind the transaction. As payment methods continue to evolve, the chip’s legacy of security and reliability will undoubtedly influence the next generation of digital finance.