Table of Contents
- What Is Near Field Communication (NFC) and Why It Matters
- Key Characteristics of NFC
- The Step‑by‑Step Journey of a Contactless Transaction
- 1. Card Detection and Activation
- 2. Data Exchange Initiation
- 3. Authentication and Cryptogram Generation
- 4. Transaction Authorization Request
- 5. Issuer Verification
- 6. Completion and Settlement
- Security Mechanisms That Keep Contactless Payments Safe
- Tokenization
- Dynamic Cryptograms
- Risk Management Limits
- EMVCo Standards
- Hardware and Software Requirements for Merchants
- Reader Types
- Impact on Consumer Experience and Merchant Operations
- Real‑World Example
- Future Trends: From Contactless Cards to Wearables and Beyond
Contactless credit card payment has become a staple of modern commerce, allowing shoppers to complete purchases with a quick tap of their card. The keyword “contactless credit card payment” captures a complex interplay of radio waves, encryption, and instant verification that happens in the blink of an eye. Understanding this process helps both consumers and merchants appreciate the convenience and security built into every tap.
Imagine standing in line at a coffee shop. You pull out your card, hold it near the terminal, and within seconds the transaction is approved. Behind that seamless experience lies a series of coordinated actions that start the moment the card enters the electromagnetic field of the reader. This narrative will walk you through each step, from the moment the card is presented to the final settlement in the bank’s ledger.
By the end of this article, you will see how Near Field Communication (NFC) technology, tokenization, and dynamic authentication work together to make contactless payments both fast and secure. Whether you’re a frequent traveler, a tech‑savvy shopper, or a merchant looking to upgrade your point‑of‑sale (POS) system, the inner workings of contactless payments are worth knowing.
What Is Near Field Communication (NFC) and Why It Matters
Contactless credit cards rely on NFC, a short‑range wireless technology that enables devices to exchange data when they are within a few centimeters of each other. NFC operates at 13.56 MHz and uses magnetic induction to create a tiny electromagnetic field. When a card is brought close to the reader, the field powers the card’s chip, allowing it to transmit information without any physical contact.
Key Characteristics of NFC
- Short Range: Typically 4 cm or less, which reduces the risk of accidental data interception.
- Bidirectional Communication: Both the card and the reader can send and receive data, enabling handshake protocols for authentication.
- Low Power Consumption: The card is passive; it draws power from the reader’s field, meaning no battery is needed.
The combination of these characteristics makes NFC ideal for quick, reliable transactions in busy retail environments.
The Step‑by‑Step Journey of a Contactless Transaction
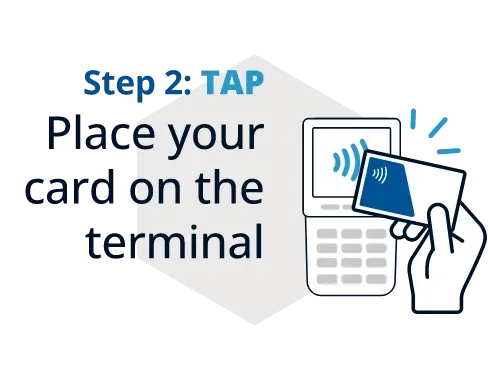
When a consumer taps a contactless card, the following sequence unfolds:
1. Card Detection and Activation
The POS terminal emits an electromagnetic field. As soon as the card enters this field, its embedded chip becomes active. The chip reads the field’s frequency and prepares to exchange data.
2. Data Exchange Initiation
The terminal sends a “poll” command, prompting the card to respond with its unique identifier, known as the PAN (Primary Account Number) token. Modern cards, however, rarely transmit the raw PAN; they send a tokenized version that replaces the actual account number with a surrogate value.
3. Authentication and Cryptogram Generation
To prove that the card is genuine, the chip generates a dynamic cryptogram—a short, encrypted code that changes with every transaction. This cryptogram is created using a secret key stored on the chip and transaction‑specific data such as the amount and a random number (nonce). Because the cryptogram is unique each time, replay attacks become virtually impossible.
4. Transaction Authorization Request
The terminal packages the tokenized PAN, cryptogram, transaction amount, and merchant identifier into an authorization request. This data is sent over a secure network to the card issuer’s processing center.
5. Issuer Verification
At the issuer’s side, the received cryptogram is decrypted using the corresponding secret key. The issuer validates the transaction details and checks the cardholder’s account status. If everything aligns, the issuer sends back an approval code.
6. Completion and Settlement
The terminal receives the approval, displays a “Approved” message, and prints a receipt if required. The transaction amount is then posted to the cardholder’s account and, later, settled between the merchant’s acquiring bank and the issuer.
This entire flow typically occurs in less than a second, creating the perception of instant payment.
Security Mechanisms That Keep Contactless Payments Safe
While speed is a major selling point, security is the foundation that keeps both consumers and merchants confident. Several layers of protection are embedded in the contactless payment process.
Tokenization
Instead of transmitting the actual PAN, the card’s chip sends a token—a random, temporary identifier. Even if a malicious actor intercepts the data, the token is useless without the issuer’s token‑mapping database.
Dynamic Cryptograms
Each transaction generates a fresh cryptogram. This dynamic element prevents replay attacks, where an intercepted transaction could be replayed later to steal funds.
Risk Management Limits
Many issuers set a “contactless limit,” typically ranging from $30 to $100, above which a PIN or signature is required. This limit mitigates the risk of fraud in case a card is lost or stolen.
EMVCo Standards
Contactless cards follow the EMV (Europay, Mastercard, Visa) specifications, which define the cryptographic algorithms, data formats, and communication protocols. Compliance with EMVCo ensures interoperability across different terminals and banks worldwide.
Hardware and Software Requirements for Merchants

Merchants must equip their POS systems with NFC‑enabled readers to accept contactless cards. These readers can be standalone devices or integrated into modern smartphones and tablets using Bluetooth or USB connections.
Reader Types
- Standalone Terminals: Rugged devices designed for high‑traffic retail environments.
- Mobile POS (mPOS): Small card readers that plug into smartphones, ideal for pop‑up shops or delivery services.
- Integrated NFC Modules: Built directly into newer cash registers and self‑service kiosks.
The software that drives these readers must support EMV contactless protocols, manage tokenization, and securely transmit data to the payment gateway. Many merchants choose cloud‑based solutions that handle encryption and compliance updates automatically.
Impact on Consumer Experience and Merchant Operations

Contactless payments have reshaped the retail landscape. For consumers, the primary benefits are speed, convenience, and reduced physical contact—a factor that gained prominence during the COVID‑19 pandemic. For merchants, faster transaction times translate into shorter queues and higher throughput, directly influencing sales volume.
Moreover, contactless cards often work alongside mobile wallets such as Apple Pay or Google Pay. These wallets store the same tokenized data and generate their own cryptograms, extending the same security model to smartphones and smartwatches.
Real‑World Example
A shopper at a grocery store taps a Visa contactless card worth $23.45. The NFC reader activates, the card sends a token and a dynamic cryptogram, the issuer validates the data, and approval is returned within 0.7 seconds. The entire process is invisible to the shopper, yet multiple encryption layers have protected the transaction.
Future Trends: From Contactless Cards to Wearables and Beyond
The technology that powers contactless cards is evolving. Emerging trends include:
- Biometric Authentication: Some next‑generation cards embed fingerprint sensors, adding a second factor without compromising speed.
- Enhanced Tokenization: Real‑time token rotation could further reduce fraud risk.
- Integration with IoT: Smart appliances may soon accept contactless payments directly, expanding the ecosystem beyond traditional POS terminals.
These innovations will continue to blur the line between physical cards and digital payment methods, but the core principles—short‑range NFC communication, tokenization, and dynamic cryptograms—will remain central.
For readers interested in a deeper dive into how different credit cards compare in value, the Which Card Wins the Cash‑Back Battle? Citi Double Cash vs Fidelity Rewards – A Detailed Comparison offers an insightful analysis. If you are managing credit card debt, the guide on How to Negotiate Credit Card Debt Settlement provides practical steps that complement responsible use of contactless payments.
In summary, the simplicity of a tap belies a sophisticated series of actions that ensure each transaction is swift, secure, and reliable. As NFC technology matures and new security layers are introduced, contactless payments will likely become even more pervasive, shaping the way we shop, travel, and interact with the digital economy.